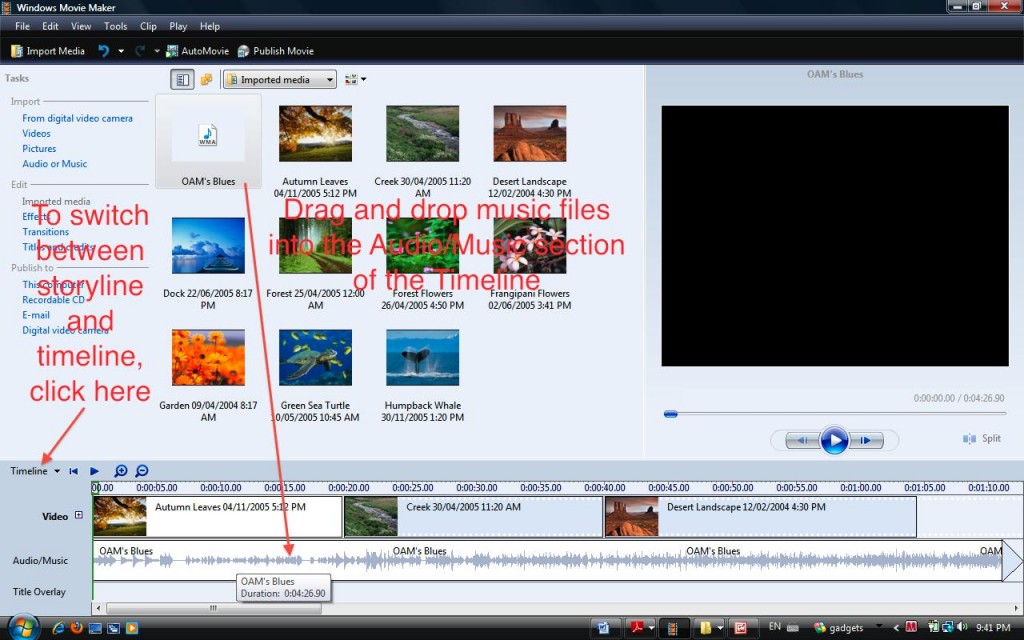
 Video. Win Movie Maker Free Download. Video. Win Movie Maker 2. Video. Win Movie Maker is a video creatingediting software application, designed for Windows 7, 8, 1. XP, Vista. Download the Best Windows Movie Maker Software for making your own movies. Key Features With Video. Win Movie Maker, its easy to organize and select the photos and videos you want to use in your next movie. With Video. Win Movie Maker, you can add text, transitions, effects, and more. Change as much as you want, or let Movie Maker do it for you. Post your movie to your favorite sitesincluding You. A beginners video tutorial on how to download Windows Movie Maker Install. See how to download Windows Movie Maker for Windows 8, Windows 8. 1 and even. Tube, Facebook, Windows Live Sky. Drive, and many others, right from Video. Win Movie Maker. Download Information. Operating System Windows XP, Windows 7, Windows 8, Windows 1. Windows Vista. Version 2. Software Price Free Trial. Windows Movie Maker rende la creazione casalinga di video semplice e divertente con questo software infatti possibile creare, montare e condividere i propri video. Compatible with Windows 7, 8, 10, XP, Vista. With Video Win Movie Maker for Windows, you can easily make your own movie from your images and videos collections. You. how to download windows movie maker in Hindi free windows movie maker download and use kaise kare Duration 550. Kaise Karen 6,254 views. Download windows 8 movie maker Windows Movie Maker Windows Vista 2. 6 The easiest way to create photo presentations, and much more programs.
Video. Win Movie Maker Free Download. Video. Win Movie Maker 2. Video. Win Movie Maker is a video creatingediting software application, designed for Windows 7, 8, 1. XP, Vista. Download the Best Windows Movie Maker Software for making your own movies. Key Features With Video. Win Movie Maker, its easy to organize and select the photos and videos you want to use in your next movie. With Video. Win Movie Maker, you can add text, transitions, effects, and more. Change as much as you want, or let Movie Maker do it for you. Post your movie to your favorite sitesincluding You. A beginners video tutorial on how to download Windows Movie Maker Install. See how to download Windows Movie Maker for Windows 8, Windows 8. 1 and even. Tube, Facebook, Windows Live Sky. Drive, and many others, right from Video. Win Movie Maker. Download Information. Operating System Windows XP, Windows 7, Windows 8, Windows 1. Windows Vista. Version 2. Software Price Free Trial. Windows Movie Maker rende la creazione casalinga di video semplice e divertente con questo software infatti possibile creare, montare e condividere i propri video. Compatible with Windows 7, 8, 10, XP, Vista. With Video Win Movie Maker for Windows, you can easily make your own movie from your images and videos collections. You. how to download windows movie maker in Hindi free windows movie maker download and use kaise kare Duration 550. Kaise Karen 6,254 views. Download windows 8 movie maker Windows Movie Maker Windows Vista 2. 6 The easiest way to create photo presentations, and much more programs.
 Should I install the 3. Microsoft Office 2. Windows IS T strongly recommends the 3. Microsoft Office the default installation on computers that are running both 3. Windows operating systems. This is due to issues with plug ins and backward compatibility. Office 2. 01. 6 6. This update for Adobe Acrobat 5. 0 provides additional compatibility and fixes known issues, including support for Microsoft Windows XP and better integration. Known Issues There is no support for Office 2. SAP GUI for Windows, only 3. Office 2. 01. 6 is supported. The 6. 4 bit version of Microsoft Office isnt compatible with any other 3. Office programs. So you must first uninstall all 3. Office programs before you install the 6.
Should I install the 3. Microsoft Office 2. Windows IS T strongly recommends the 3. Microsoft Office the default installation on computers that are running both 3. Windows operating systems. This is due to issues with plug ins and backward compatibility. Office 2. 01. 6 6. This update for Adobe Acrobat 5. 0 provides additional compatibility and fixes known issues, including support for Microsoft Windows XP and better integration. Known Issues There is no support for Office 2. SAP GUI for Windows, only 3. Office 2. 01. 6 is supported. The 6. 4 bit version of Microsoft Office isnt compatible with any other 3. Office programs. So you must first uninstall all 3. Office programs before you install the 6.  Adobe is changing the world through digital experiences. We help our customers create, deliver and optimize content and applications. Original Title Housewife Adobe Acrobat Reader DC not working with Windows 10 64bit. Adobe Document Cloud insights, trends, news and more. Learn about software and hardware requirements for Adobe Acrobat Reader DC. Heres the entire set of all Adobe CC 2015 Updates, the direct links you can download to upgrade your Creative Cloud 2015 tools on Windows.
Adobe is changing the world through digital experiences. We help our customers create, deliver and optimize content and applications. Original Title Housewife Adobe Acrobat Reader DC not working with Windows 10 64bit. Adobe Document Cloud insights, trends, news and more. Learn about software and hardware requirements for Adobe Acrobat Reader DC. Heres the entire set of all Adobe CC 2015 Updates, the direct links you can download to upgrade your Creative Cloud 2015 tools on Windows.  Office. Any add ins you want to run for Office must also be 6. Active. X controls library, Com. Ctl. Any solutions using these controls dont work. No good alternatives are available for some of these controls. Third party 3. 2 bit Active. X controls and add ins. None of these work with the 6. Office. There is no 6. Visual Basic 6, so many of these objects need to be ported and rewritten. Microsoft Visual Basic for Applications VBA VBA only contains the Declare statement work in the 6. Office if you update the code manually. Compiled Access databases The. MDE and. ACCDE files, a common way for Access application developers to distribute solutions and protect their intellectually property, dont work in the 6. Office. You must contact the application developer to recompile, retest, and redistribute the solution in the 6. The only users that are likely to gain advantage from the 6. Excel spreadsheets. Unless you are engaging in such computationally intensive activities with Office, the 3. Learn more about deployment considerations for 6. Office 2. 01. 6 from Microsoft support. The 3. 2 bit version of Office is strongly recommended. PDF XChange Editor 6. Free download and software reviews. Pros. Quickly imports pdf files from images and other pdf files. Cons. The license expired, but when I purchased it they didnt make clear that I was only renting the software. Reply to this review. Was this review helpful 1. Pros. I was looking for a simple PDF editorwriter to blank out certain details that i dont want to share in a PDF. For example, removing social security numbers. This software does this well enough. Cons. I selected the option to appear in browser or something like that. I initially didnt know what this meant. Now this app tries to open when I launch PDFs in my browser and I have been through all of the app settings and cant find a way to disable it. The problem is that it doesnt work for some sites so I can no longer view pdf from certain siites. Reply to this review. Was this review helpful 1. Pros. It displays some parts correctly, but most texts disappear from the moment I open the PDF. Cons. Most texts are not displayed. So I cannot use it. Perhaps the developer needs to improve this software. Reply to this review. Was this review helpful 1. Pros. Great basic pdf editor. Covers all of our PDF requirements easily and efficiently. Cons. That I didnt find it earlier One third the price of Bluebeam which after a month of owning it now wants another 1. Summary. Paper size took a while to figure out but other than that it is a well written program. No PDF printer included but the free Cutepdf printer works well. Very happy with product. Reply to this review. Was this review helpful 1. Pros. This Editor is new product and I decided to try it because I work with other tracker software products. These previous are excellent but now I like Editor much more. Very nice UI, very nice and easy to do my works with pdfs. Feature kit are wider than Viewer kit and I can use my licence key from Viewer. For example, in Editor I like more features for work with document redaction, signing, header footer, numbering, OCR, comments import export, scanning, forms and sending files to e mail, very fast searching words in huge pdf folders etc. Im surprised, price is still enough cheap. Cons. Waiting for some new features. But no cons for existing. Summary. Big part in my work is work with pdfs and I can say today PDF XChange Editor is the best thing for that. Even you dont want to buy, you can use its many free features and also try non free features. Reply to this review. Was this review helpful 1. Pros. Its fast, loads PDF files quickly, renders really nicely and I love the mark up tools. The OCR feature is great, I especially like the way it can OCR during a scan. Editing the PDF itself. I was blown away when I realized I could edit the PDF itself, not just the annotations. The editing is really nicely done, much more intuitive and easier to use than others I tried. The license allows me to install on both a workstation and a laptop so I can have it with me when on the road I really like that. Cons. Not sure if its a con but I wanted to use the New Document Combine files into a single PDF feature but it required a license. That would have been nice if it were a free feature. Summary. This is the best PDF package for the money anywhere. Period. I wanted to use some of the pro features so I shelled out the 4. Reply to this review. Was this review helpful 1. Pros. I have tested several alternative PDF viewing tools and must say the Tracker products are the best ones Ive found. The Editor has all the features I need and even more that I will probably not use but its nice that you have the options. Cons. I cant think of any major drawbacks maybe some things are not yet exactly the same as in the previous product they had the Viewer hence the 4. Once those are fixed it will be a truly 5 star product Summary. I use the Editor daily and it is really helping me with all my with the multitude of files I have to handle every day Give it a try people you will not regret it Reply to this review. Was this review helpful 1. Pros. Great OCRContent editing works like a charm. Reasonably priced for licensed version around 4. Love the annotaions and the ability to add different colors of tools to the toolbar. VERY fast Great search function tested with a 2. GB, 1. 75. 00 page file searched for a Adobe takes 2. Foxit Nitro crash, Editor takes 5minsTheres a lot more that I love, but I wont bore you Cons. OCR doesnt prodcue editable text. Support staff say this is in the works though. No 3. D rendering yet. Installers are on the larger side. No portable version yet. Summary. I love it I read a lot of scientific papers and regulary need to search for specific topics, then highlight portions of the text and link notes to those portions. This is extremely easy to do and intuitive, so it makes my days easier I also like to use different colored notes and highlights, to make things stand out more. In the Viewer, I could setup different styles for each comment, but had to open up the palette to switch colors. I love that, in the Editor, I can place multiple styles of the same tool on the toolbar, then assign each its own unique shortcut far smoother. Would and do highly recommend this over any other. Cant stand Adobe or Nitro both are clunky and crash constantly. Never used Foxit. Reply to this review. Was this review helpful 1. Pros. Free Version allows direct text editing of text based pdfs no charge. Price for license under 5. USD. licensed feature Redaction worked great. Free OCR for PDF created from my scanner, makes my scans searchable love it. Cons. Cant OCR a scan based pdf to an editable PDF, I contacted the publisher of the software and it is in the worksCnet download of the installer was full of crappy toolbars and offers, but when U downloaded the installer from Tracker Softwares site none of that is included, Ive noticed this in other downloads from CNET too, thats too bad. Summary. I use this product for Sheet music and Bass Tablature, I was surprised at how great this software is can make custom stamps of music notes and markup up sheetmusic scores I cant until I can scan sheet music and tablature and ocr it so I can directly edit it, but I was told thats coming in a plugin for the Editor, The price I paid for a license was only 4. USD and it included a free PDF printer too, which produces PDFs you can then edit with the Editor. Super Bargain for quality product. Cant say that very often these days. Beats adobe hands down. Reply to this review. Was this review helpful 1.
Office. Any add ins you want to run for Office must also be 6. Active. X controls library, Com. Ctl. Any solutions using these controls dont work. No good alternatives are available for some of these controls. Third party 3. 2 bit Active. X controls and add ins. None of these work with the 6. Office. There is no 6. Visual Basic 6, so many of these objects need to be ported and rewritten. Microsoft Visual Basic for Applications VBA VBA only contains the Declare statement work in the 6. Office if you update the code manually. Compiled Access databases The. MDE and. ACCDE files, a common way for Access application developers to distribute solutions and protect their intellectually property, dont work in the 6. Office. You must contact the application developer to recompile, retest, and redistribute the solution in the 6. The only users that are likely to gain advantage from the 6. Excel spreadsheets. Unless you are engaging in such computationally intensive activities with Office, the 3. Learn more about deployment considerations for 6. Office 2. 01. 6 from Microsoft support. The 3. 2 bit version of Office is strongly recommended. PDF XChange Editor 6. Free download and software reviews. Pros. Quickly imports pdf files from images and other pdf files. Cons. The license expired, but when I purchased it they didnt make clear that I was only renting the software. Reply to this review. Was this review helpful 1. Pros. I was looking for a simple PDF editorwriter to blank out certain details that i dont want to share in a PDF. For example, removing social security numbers. This software does this well enough. Cons. I selected the option to appear in browser or something like that. I initially didnt know what this meant. Now this app tries to open when I launch PDFs in my browser and I have been through all of the app settings and cant find a way to disable it. The problem is that it doesnt work for some sites so I can no longer view pdf from certain siites. Reply to this review. Was this review helpful 1. Pros. It displays some parts correctly, but most texts disappear from the moment I open the PDF. Cons. Most texts are not displayed. So I cannot use it. Perhaps the developer needs to improve this software. Reply to this review. Was this review helpful 1. Pros. Great basic pdf editor. Covers all of our PDF requirements easily and efficiently. Cons. That I didnt find it earlier One third the price of Bluebeam which after a month of owning it now wants another 1. Summary. Paper size took a while to figure out but other than that it is a well written program. No PDF printer included but the free Cutepdf printer works well. Very happy with product. Reply to this review. Was this review helpful 1. Pros. This Editor is new product and I decided to try it because I work with other tracker software products. These previous are excellent but now I like Editor much more. Very nice UI, very nice and easy to do my works with pdfs. Feature kit are wider than Viewer kit and I can use my licence key from Viewer. For example, in Editor I like more features for work with document redaction, signing, header footer, numbering, OCR, comments import export, scanning, forms and sending files to e mail, very fast searching words in huge pdf folders etc. Im surprised, price is still enough cheap. Cons. Waiting for some new features. But no cons for existing. Summary. Big part in my work is work with pdfs and I can say today PDF XChange Editor is the best thing for that. Even you dont want to buy, you can use its many free features and also try non free features. Reply to this review. Was this review helpful 1. Pros. Its fast, loads PDF files quickly, renders really nicely and I love the mark up tools. The OCR feature is great, I especially like the way it can OCR during a scan. Editing the PDF itself. I was blown away when I realized I could edit the PDF itself, not just the annotations. The editing is really nicely done, much more intuitive and easier to use than others I tried. The license allows me to install on both a workstation and a laptop so I can have it with me when on the road I really like that. Cons. Not sure if its a con but I wanted to use the New Document Combine files into a single PDF feature but it required a license. That would have been nice if it were a free feature. Summary. This is the best PDF package for the money anywhere. Period. I wanted to use some of the pro features so I shelled out the 4. Reply to this review. Was this review helpful 1. Pros. I have tested several alternative PDF viewing tools and must say the Tracker products are the best ones Ive found. The Editor has all the features I need and even more that I will probably not use but its nice that you have the options. Cons. I cant think of any major drawbacks maybe some things are not yet exactly the same as in the previous product they had the Viewer hence the 4. Once those are fixed it will be a truly 5 star product Summary. I use the Editor daily and it is really helping me with all my with the multitude of files I have to handle every day Give it a try people you will not regret it Reply to this review. Was this review helpful 1. Pros. Great OCRContent editing works like a charm. Reasonably priced for licensed version around 4. Love the annotaions and the ability to add different colors of tools to the toolbar. VERY fast Great search function tested with a 2. GB, 1. 75. 00 page file searched for a Adobe takes 2. Foxit Nitro crash, Editor takes 5minsTheres a lot more that I love, but I wont bore you Cons. OCR doesnt prodcue editable text. Support staff say this is in the works though. No 3. D rendering yet. Installers are on the larger side. No portable version yet. Summary. I love it I read a lot of scientific papers and regulary need to search for specific topics, then highlight portions of the text and link notes to those portions. This is extremely easy to do and intuitive, so it makes my days easier I also like to use different colored notes and highlights, to make things stand out more. In the Viewer, I could setup different styles for each comment, but had to open up the palette to switch colors. I love that, in the Editor, I can place multiple styles of the same tool on the toolbar, then assign each its own unique shortcut far smoother. Would and do highly recommend this over any other. Cant stand Adobe or Nitro both are clunky and crash constantly. Never used Foxit. Reply to this review. Was this review helpful 1. Pros. Free Version allows direct text editing of text based pdfs no charge. Price for license under 5. USD. licensed feature Redaction worked great. Free OCR for PDF created from my scanner, makes my scans searchable love it. Cons. Cant OCR a scan based pdf to an editable PDF, I contacted the publisher of the software and it is in the worksCnet download of the installer was full of crappy toolbars and offers, but when U downloaded the installer from Tracker Softwares site none of that is included, Ive noticed this in other downloads from CNET too, thats too bad. Summary. I use this product for Sheet music and Bass Tablature, I was surprised at how great this software is can make custom stamps of music notes and markup up sheetmusic scores I cant until I can scan sheet music and tablature and ocr it so I can directly edit it, but I was told thats coming in a plugin for the Editor, The price I paid for a license was only 4. USD and it included a free PDF printer too, which produces PDFs you can then edit with the Editor. Super Bargain for quality product. Cant say that very often these days. Beats adobe hands down. Reply to this review. Was this review helpful 1.
Watch Movies Online Free in HD at Watch. Download Adventure Fishing 2 1 Keygen Download For Ets2Watch32 Watch Movies on Watch32. com Watch32 is the Biggest Library of free Full Movies. Watch 32 Movies Online. Think more Creatively. The Philippines, being a country archipelago of islands and seas, have naturally wonderful beaches, some of which are famous the world over. Beaches like Puerto. Google is compensated by these merchants. Payment is one of several factors used to rank these results. Tax and shipping costs are estimates. Kilauea Mount Etna Mount Yasur Mount Nyiragongo and Nyamuragira Piton de la Fournaise Erta Ale. How To Build A Pole Building Step By Step 12 X 20 Storage Building Lynchburg Va How To Build A Pole Building Step By Step Diy Run In Sheds Garden Sheds At Walmart. Download Adventure Fishing 2 1 Keygen Download For SonyYou have not yet voted on this site If you have already visited the site, please help us classify the good from the bad by voting on this site. Statistical Techniques Statistical Mechanics. b i was a girl with flowers in my hair. fuck movies black and blond. trident video accelerator cyberblade xp treiber. b urlhttpfreemovies11. ruhotmovies. Hotwapi. Com is a mobile toplist for mobile web sites. We have over 2000 registered sites.
Headlines 2. Ron Paul Tillerson Laid Out A Raving Neocon Foreign Policy In His Senate Hearing US Intel Try To StrongArm Trump Into Russian War. PS3 Cheats Call of Duty Black Ops This page contains a list of cheats, codes, Easter eggs, tips, and other secrets for Call of Duty Black Ops for. Moon Call of Duty Black Ops Moon is the last zombie map for Call of Duty Black Ops. It takes place at Area 51 Groom Lake and allows you to teleport. Loading screen in Call of Duty Black Ops. Main article Der Riese The Giant is rising. Face the might of the Nazi Zombies in their heartland. This is where it all. Games. RadarGames. Radar is part of Future plc, an international media group and leading digital publisher. Visit our corporate site. Never let it be said that Im an impressionable twentysomethinggamingmedia prick. If I reviewed every bloody game people told me to I wouldnt even have the free. Its increasingly difficult to do anything on your phone nowadays without sharing your geolocation information. Certain Snapchat filters, Facebook status updates. Avengers The Initiative was a comic book series from Marvel Comics. Written by Dan Slott and Christos Gage with artwork initially by Stefano Caselli, Steve Uy and. 
 Initially, it appeared that the recent HBO hack was most impactful for the theft and possible leak of Game of Thrones data. The digital thieves also allegedly. Get your Concealed Weapons Permit at Orlando Gun Club This class has been developed to meet the standard requirements established in the Florida. Gordon Freeman, Ph. D., is the silent protagonist of the HalfLife series, and the playable character in HalfLife, and all games in the HalfLife 2 series. Illinois Wants To Ban Location Tracking Without Consent. Its increasingly difficult to do anything on your phone nowadays without sharing your geolocation information. Certain Snapchat filters, Facebook status updates, Instagrams, and even text messages are all potentially tied to geolocation data. Its relatively simple for app developers to build in geolocation functionalityand many services require users to opt in to sharing location data. But now the state of Illinois wants ensure that all companies extracting geolocation data from individuals must provide an opt in, or else theyll have to pay up. Last week, both houses of the Illinois state legislature passed the Geolocation Privacy Protection Act HB3. Now, its on the desk of Governor Bruce Rauner, waiting to be signed into law. If signed, companies would be required to inform users of how theyre using the location data they collect, if the users decides to share it. Companies who dont adhere would be in violation of the Consumer Fraud and Deceptive Business Practices Act and would face criminal penalties and damages of at least 1,0. There are a few exceptions to the law. For instance, private entities can collect geolocation data without consent if the information will help parents find missing children or aid firefighters, police, or medical professionals. The new law might not have a huge real world impact, given that most devices and apps already ask people for permission before they start using location data. But this might encourage more tech companies and app developers to give users the option to opt out of being tracked. There have been plenty of times in the past when companies have faced repercussions for tracking users without their consent. For instance, Apple and Uber have been sued for allegedly tracking un notified users. Ari Scharg, director of the Digital Privacy Alliance DPA, told Gizmodo that the organization has done reports on the apps Selfie. Rate Selfie Pic Hot Or Not, which give developers precise GPS coordinates whenever a person uploads a photo. When a person is just browsing through the photos to rate them, if they were intercepting the backend traffic, they would be able to get the GPS coordinates of each person they viewed, Scharg said. Overall, a person could use this information to stalk someone or the owner of the picture could retaliate against a person that left a bad comment if they were capturing the traffic. The DPA urges app developers to be transparent with users by clarifying how location data is being used. The organization has been advocating for the bill, and even wrote an open letter to Governor Rauner, which was signed by more than 2. Chicago area tech companies. Illinois has a reputation of passing strict data privacy legislation. The states Biometric Information Privacy Act prohibits tech companies from using biometric identifierslike face scans and fingerprintswithout consent. Their Right To Know Actwhich passed in May, but was put on holdrequires companies such as Facebook, Amazon, and Google to disclose what data has been collected from consumers and shared with third parties. Naked Security.
Initially, it appeared that the recent HBO hack was most impactful for the theft and possible leak of Game of Thrones data. The digital thieves also allegedly. Get your Concealed Weapons Permit at Orlando Gun Club This class has been developed to meet the standard requirements established in the Florida. Gordon Freeman, Ph. D., is the silent protagonist of the HalfLife series, and the playable character in HalfLife, and all games in the HalfLife 2 series. Illinois Wants To Ban Location Tracking Without Consent. Its increasingly difficult to do anything on your phone nowadays without sharing your geolocation information. Certain Snapchat filters, Facebook status updates, Instagrams, and even text messages are all potentially tied to geolocation data. Its relatively simple for app developers to build in geolocation functionalityand many services require users to opt in to sharing location data. But now the state of Illinois wants ensure that all companies extracting geolocation data from individuals must provide an opt in, or else theyll have to pay up. Last week, both houses of the Illinois state legislature passed the Geolocation Privacy Protection Act HB3. Now, its on the desk of Governor Bruce Rauner, waiting to be signed into law. If signed, companies would be required to inform users of how theyre using the location data they collect, if the users decides to share it. Companies who dont adhere would be in violation of the Consumer Fraud and Deceptive Business Practices Act and would face criminal penalties and damages of at least 1,0. There are a few exceptions to the law. For instance, private entities can collect geolocation data without consent if the information will help parents find missing children or aid firefighters, police, or medical professionals. The new law might not have a huge real world impact, given that most devices and apps already ask people for permission before they start using location data. But this might encourage more tech companies and app developers to give users the option to opt out of being tracked. There have been plenty of times in the past when companies have faced repercussions for tracking users without their consent. For instance, Apple and Uber have been sued for allegedly tracking un notified users. Ari Scharg, director of the Digital Privacy Alliance DPA, told Gizmodo that the organization has done reports on the apps Selfie. Rate Selfie Pic Hot Or Not, which give developers precise GPS coordinates whenever a person uploads a photo. When a person is just browsing through the photos to rate them, if they were intercepting the backend traffic, they would be able to get the GPS coordinates of each person they viewed, Scharg said. Overall, a person could use this information to stalk someone or the owner of the picture could retaliate against a person that left a bad comment if they were capturing the traffic. The DPA urges app developers to be transparent with users by clarifying how location data is being used. The organization has been advocating for the bill, and even wrote an open letter to Governor Rauner, which was signed by more than 2. Chicago area tech companies. Illinois has a reputation of passing strict data privacy legislation. The states Biometric Information Privacy Act prohibits tech companies from using biometric identifierslike face scans and fingerprintswithout consent. Their Right To Know Actwhich passed in May, but was put on holdrequires companies such as Facebook, Amazon, and Google to disclose what data has been collected from consumers and shared with third parties. Naked Security.
How to use Reaver to crack WPA2 Passwords with a 99 success rate. Most users will be smart and set up their router with WPA encryption. Now what would happen if you tried to connect a device that only supports WEP, for example a PDA. Popular Wireless Hacking Tools updated for 2. Last year, I wrote an article covering popular wireless hacking tools to crack or recover password of wireless network. We added 1. 3 tools in that article which were popular and work great. Now I am updating that post to add few more in that list. I will not explain about wireless security and WPAWEP. You can read the existing article on wireless hacking tools to learn about them. In this post, I am updating the existing list to add few more powerful tools. I am adding seven new tools in the existing list to give you a single list of the most used wireless cracking tools. Aircrack. Aircrack is the most popular and widely known wireless password cracking tool. It is used as 8. 02. WEP and WPA PSK keys cracking tool around the globe. It first captures packets of the network and then try to recover password of the network by analyzing packets. It also implements standard FMS attacks with some optimizations to recover or crack password of the network. Kore. K attacks and PTW attack to make the attack much faster than other WEP password cracking tools. This tool is powerful and used most widely across the world. This is the reason I am adding it at the top of the list.  WEP cracking is not an exact science. The number of required IVs depends on the WEP key length, and it also depends on your luck. Usually, 40bit WEP 64 bit key can. Standard 64bit WEP uses a 40 bit key also known as WEP40, which is concatenated with a 24bit initialization vector IV to form the RC4 key. How to Break WEP Encryption. Breaking any encryption coding or codes involves knowing a few things. First, you have to know that there is an encryption scheme. Website dedicated to Wireless LAN Security and Wardriving. Includes lots of whitepapers, presentations, tools, firmware, drivers, equipment, and resources. Were constantly telling you that using WEP to secure your wireless network is really a fools game, yet people still do it. Today Id like to show you exactly. Last year, I wrote an article covering popular wireless hacking tools to crack or recover password of wireless network. We added 13 tools in that article which were.
WEP cracking is not an exact science. The number of required IVs depends on the WEP key length, and it also depends on your luck. Usually, 40bit WEP 64 bit key can. Standard 64bit WEP uses a 40 bit key also known as WEP40, which is concatenated with a 24bit initialization vector IV to form the RC4 key. How to Break WEP Encryption. Breaking any encryption coding or codes involves knowing a few things. First, you have to know that there is an encryption scheme. Website dedicated to Wireless LAN Security and Wardriving. Includes lots of whitepapers, presentations, tools, firmware, drivers, equipment, and resources. Were constantly telling you that using WEP to secure your wireless network is really a fools game, yet people still do it. Today Id like to show you exactly. Last year, I wrote an article covering popular wireless hacking tools to crack or recover password of wireless network. We added 13 tools in that article which were. 
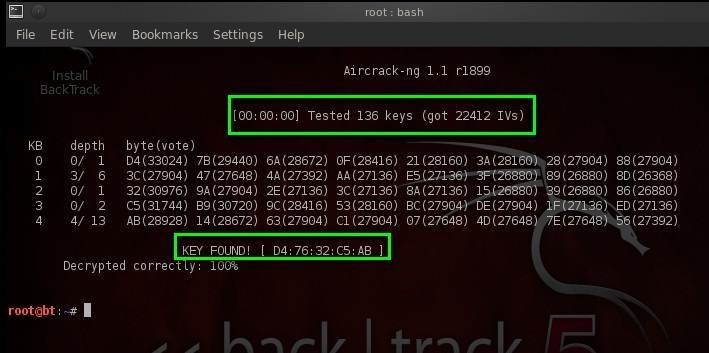 Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired. It offers console interface. If you find this tool hard to use, you can try the available online tutorials. Company behind this tool also offers online tutorial to let you learn by yourself. Download http www. Air. Snort. Air. Snort is another popular wireless LAN password cracking tool. It can crack WEP keys of Wi Fi. This tool basically operates by passively monitoring transmissions and then computing the encryption key when enough packets have been gathered. This tool is freely available for Linux and Windows platform. It is also simple to use. The tool has not been updated for around three years, but it seems that company behind this tool is now interested in further development. This tool is also directly involved in WEP cracking and hence used widely. Download Air. Snort http sourceforge. Kismet. Kismet is another Wi Fi 8. This tool is basically used in Wi Fi troubleshooting. It works fine with any Wi Fi card supporting rfmon mode. It is available for Windows, Linux, OS X and BSD platforms. This tool passively collects packets to identify standard network and also detects the hidden networks. Built on a client server modular architecture, this tool can sniff 8. It is an open source tool and supports recent faster wireless standards. Download Kismet http www. Ethical Hacking Training Resources Info. Sec4. Cain Able. Cain Able is another popular tool used for cracking wireless network passwords. This tool was developed to intercept the network traffic and then use the brute forcing to discover the passwords. This is why this tool helps a lot while finding the password of wireless network by analyzing the routing protocols. This tool can also be used to crack other kind of passwords. It is one of the most popular password cracking tools. This tool is not just for WEP cracking but various other features are also there. It is basically used for Windows password cracking. This is the reason this tool is so popular among users. Download Cain Able http www. Wire. Shark. Wire. Shark is a very popular tool in networking. It is the network protocol analyzer tool which lets you check different things in your office or home network. You can live capture packets and analyze packets to find various things related to network by checking the data at the micro level. This tool is available for Windows, Linux, OS X, Solaris, Free. BSD and other platforms. If you are thinking to try this tool, I recommend you to first read about networking and protocols. Wire. Shark requires good knowledge of network protocols to analyze the data obtained with the tool. If you do not have good knowledge of that, you may not find this tool interesting. So, try only if you are sure about your protocol knowledge. Wireshark does is one of the most popular tool in networking and this is why it was included in this list in higher position. Download Wireshark https www. Fern Wi. Fi Wireless Cracker. Fern Wi. Fi Wireless Cracker is another nice tool which helps with network security. It lets you see real time network traffic and identify hosts. Basically this tool was developed to find flaws in computer networks and fixes the detected flaws. It is available for Apple, Windows and Linux platforms. WEPWPAWPS keys easily. It can also run other network based attacks on wireless or Ethernet based networks. For cracking WPAWPA2, it uses WPS based on dictionary based attacks. For WEP cracking, it uses Fragmentation, Chop Chop, Caffe Latte, Hirte, ARP Request Replay or WPS attack. This tool is in active development. SO, you can expect timely update with new features. Pro version of the tool is also available which offers much features. Download Fern Wi. Fi Wireless cracker http www. Co. WPAtty. Co. WPAtty is another nice wireless password cracking tool. It is an automated dictionary attack tool for WPA PSK to crack the passwords. It runs on Linux OS and offers a less interesting command line interface to work with. It runs on a word list containing thousands of password to use in the attack. If the password is in the passwords word list, this tool will surely crack the password. But this tool is slow and speed depends on the word list and passwords strength. Another reason for slow process is that the hash uses SHA1 with a seed of SSID. It means the same password will have a different SSIM. So, you cannot simply use the rainbow table against all access points. So, the tool uses the password dictionary and generates the hash for each word contained in the dictionary by using the SSID. This tool is simple to use with available commands. With the newer version of the tool Co. WPAtty tried to improve the speed by using a pre computed hash file to avoid the computation at the time of cracking. This pre computed file contains around 1. SSIDs. But for successful attack, your SSID must be in that list. If your SSID is not in those 1. Still, you can try this tool to see how it works. Download Co. WPAtty http sourceforge. Airjack. Airjack is a Wi Fi 8. It is used to perform DOS attack and MIM attack. This wireless cracking tool is very useful in injecting forged packets and making a network down by denial of service attack. This tool can also be used for a man in the middle attack in the network. This tool is popular and powerful both. Download Air. Jack http sourceforge. Wep. Attack. Wep. Attack is another working open source Linux tool for breaking 8. WEP keys. Like few other tools in the list, this tool also performs an active dictionary attack. It tests millions of words from its dictionary to find the working key for the network. Only a working WLAN card is required to work with Wep. Attack to perform the attack. Limited usability but works awesome on supported WLAN cards. Download Wep. Attack http wepattack. Net. Stumbler. Net. Stumbler is another wireless password cracking tool available only for Windows platform. It helps in finding open wireless access points. This tool is freely available. Basically Net. Stumbler is used for wardriving, verifying network configurations, finding locations with a poor network, detecting unauthorized access points, and more. This tool is not very effective now. Main reason is that last stable release of the tool was back in April 2. So, it does not work with 6. AircrackAireplay ng Under Packet Injection Monitor Mode in Windows. Update 6 2. 7 0. I just found out that the makers of aircrack ng just made this method easier. Two days after I wrote this article, they released a VMWare image of their entire suite of wireless penetration tools. So, instead of downloading and using the generic Back. Track ISO step 1 and 5 head over to Aircrack ng and obtain their version. Update II 6 2. 7 0. I guess packet injection under Windows is feasible after all The same time the VMWare aircrack ng image was released, they also revealed a new USB Wi. Fi adaptor that lets you inject and read packets natively in Windows without the virtualization layer. Whats more, you can use the Wireshark GUI instead of the aircrack ng command line. Personally, I would still go with the Alfa read more below since it has nantenna connector. But thats just me WEP enabled access point within a couple of minutes. That Digg article piqued our curiosity in high school. My friend and I read about how the FBI publicly demonstrated a successful wireless network crack in a minuscule amount of time. Inspired, we obtained a laptop and searched around our neighborhood for WEP encrypted wireless networks. Our plan was to show these local folks how easy it was to acquire their WEP key. Then, we would convince them that we were good, hirable technicians who could upgrade their Wi. Fi WEP encryption scheme to WPA. We spent literally three days practicing, trying to crack our own network with Windows tools. But in the end, our plan never materialized. Why We were too n. Linux. Crippled Windows Users. Ill say it once and Ill say it again, I hate being a Windows user. I hold great respect for computer hackers who are quick to grasp other operating systems, like Linux and OS X, without a problem. But I, having been weaned on Windows since the day I touched a computer, have a hard time operating those unfamiliar user interfaces or lack thereof. I mean, more than half of Linux is in the shell command line Aircrack ng Win. Binary Port. Many users like myself have a hard time integrating with the computer hacker world. Most programs are written for nix operating systems. Only when a kind, talented soul takes pity on us Windows amateurs and ports the code to Win. At the time, that Win. Even today, wireless network penetration software is still in the Linux stage. The main software suite, Aircrack ng, is just barely supported in Windows. When I tried the Windows port, it was slow, it did not accept my drivers, and it crashed numerous times. Basically, the Win. Virtualization Solution. Finally, I decided to just try aircrack ng in Linux. I bought some equipment and ran the Backtrack Live on CD Linux Distribution. After reading up on numerous Linux and aircrack ng documentation, I was finally able to crack my home network While I was writing about hacking the Windows Vista and t mobile free Wireless Internet authentication which is not no longer relevant with VMWare, I had an epiphany. The same technique I used with VMware could also be applied to aircrack ng I tried it out and after a lot of trial and error, I cracked my home network once again. This time it was in WindowsFrequently Asked Questions. So how did I do this Before you begin my tutorial, I suggest you read this FAQ for background information. Why aircrack ng Aircrack ng is the most popular wireless cracking suite. Because of that, it is the most compatible with different types of hardware, it offers more forum support, and it is on the cutting edge of the latest Wi. Fi hacking techniques. What are the main elements in cracking a wireless network Airodump ng Gather special faulty data necessary to crack a network. Aireplay ng Stimulate the base AP station to generate the special data for aireplay ng. Aircrack ng Take the data from airodump ng and, with statistical or brute force dictionary analysis, crack the keyPSK. Why is Windows inherently unable to crack wireless networks Special mostly unavailable patched drivers are required to use these programs. What about the Peek DriverFirst of all, the Peek Driver is special software written by the Wild. Pakets Airo. Peek, sort of a wireless network version of WiresharkEthereal. The bad thing about the Peek Driver is that it only allows you to read packets. Essentially, you can only use airodump ng and aircrack ng. Theoretically, you can crack a wireless network with only these two programs but it is very difficult, drawn out, and plain inefficient. Without the speeding aid of aireplay ng, cracking a wireless network may take days. Aireplay ng helps inject packets and manipulate the wireless network. Why does the Peek Driver not support aireplay ng This is because aireplay ng requires the network card to be in a special state called Monitor Mode. In normal operation, the network interface is in Managed Mode. The Windows NDIS API Network Driver Interface Specification does not support any extensions for wireless monitor mode. Therefore, the only drivers that allow Wi. Fi cards to be in monitor mode are in Linux. Ive heard of Windows tools that support packet injection. I have too. But I also heard that they cost upwards of 3. So then there still is a way to use aireplay ng in Windows with your hack Yes. Basically, you run Backtrack as a virtual machine in VMWare Player. Since VMWare supports passthrough USB, the Backtrack virtual machine can directly access a compatible USB wireless network adapter. Note that my method will only work with a USB adapter since the only passthrough that virtual machine programs support is with the USB interface, not PCI, mini. PCI, PCMCIA, PC Card, Express Card, etc. So, I wont need to know Linux commands and I will be presented with that familiar, friendly user interface that I am accustomed to in Windows Heavens no If you read the answer above, you know you will still be using Linux in Windows. This is just a convenience of not having to switch between reboots. You will still be unable to avoid the obscure Linux shell commands Hardware. Lets just cut to the chase. There is no reason to continue if you dont even own the correct hardware. Im sorry, but there is no workaround for this. Im a frugal person and I tried doing this the frugal way. It just doesnt work. If youre not willing to open your wallet, I would stop reading now. In my research and tests on compatible network adapters, there is only one with the least quirks and the least breakage for this operation. Get the Alfa USB AWUS0. S Network Adaptor with the threaded RP SMA antenna connector. USB Wi. Fi adapters with antenna connections are almost impossible to find. Usually you have to solder and mod the circuitry of another adapter to gain this functionality. Save yourself some trouble and just purchase this one. Now, if you could only find where to buy this elusive piece of equipment. I found mine at Data. Alliance, an onlinee. Bay store managed by a man name George Hardesty. If you know of any other worthy store, please comment at the end of this post. Hardesty supplies most of my wireless networking needs. His inventory is the most cutting edge and cheapest that I have come across. Take a look at his store. It includes one of the most comprehensive resources Ive read on wireless networking. Nevertheless, dont be tempted to purchase the high powered Alfa USB AWUS0. H WLAN Adapter. Ive used it twice It breaks easily and it is noisy.
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired. It offers console interface. If you find this tool hard to use, you can try the available online tutorials. Company behind this tool also offers online tutorial to let you learn by yourself. Download http www. Air. Snort. Air. Snort is another popular wireless LAN password cracking tool. It can crack WEP keys of Wi Fi. This tool basically operates by passively monitoring transmissions and then computing the encryption key when enough packets have been gathered. This tool is freely available for Linux and Windows platform. It is also simple to use. The tool has not been updated for around three years, but it seems that company behind this tool is now interested in further development. This tool is also directly involved in WEP cracking and hence used widely. Download Air. Snort http sourceforge. Kismet. Kismet is another Wi Fi 8. This tool is basically used in Wi Fi troubleshooting. It works fine with any Wi Fi card supporting rfmon mode. It is available for Windows, Linux, OS X and BSD platforms. This tool passively collects packets to identify standard network and also detects the hidden networks. Built on a client server modular architecture, this tool can sniff 8. It is an open source tool and supports recent faster wireless standards. Download Kismet http www. Ethical Hacking Training Resources Info. Sec4. Cain Able. Cain Able is another popular tool used for cracking wireless network passwords. This tool was developed to intercept the network traffic and then use the brute forcing to discover the passwords. This is why this tool helps a lot while finding the password of wireless network by analyzing the routing protocols. This tool can also be used to crack other kind of passwords. It is one of the most popular password cracking tools. This tool is not just for WEP cracking but various other features are also there. It is basically used for Windows password cracking. This is the reason this tool is so popular among users. Download Cain Able http www. Wire. Shark. Wire. Shark is a very popular tool in networking. It is the network protocol analyzer tool which lets you check different things in your office or home network. You can live capture packets and analyze packets to find various things related to network by checking the data at the micro level. This tool is available for Windows, Linux, OS X, Solaris, Free. BSD and other platforms. If you are thinking to try this tool, I recommend you to first read about networking and protocols. Wire. Shark requires good knowledge of network protocols to analyze the data obtained with the tool. If you do not have good knowledge of that, you may not find this tool interesting. So, try only if you are sure about your protocol knowledge. Wireshark does is one of the most popular tool in networking and this is why it was included in this list in higher position. Download Wireshark https www. Fern Wi. Fi Wireless Cracker. Fern Wi. Fi Wireless Cracker is another nice tool which helps with network security. It lets you see real time network traffic and identify hosts. Basically this tool was developed to find flaws in computer networks and fixes the detected flaws. It is available for Apple, Windows and Linux platforms. WEPWPAWPS keys easily. It can also run other network based attacks on wireless or Ethernet based networks. For cracking WPAWPA2, it uses WPS based on dictionary based attacks. For WEP cracking, it uses Fragmentation, Chop Chop, Caffe Latte, Hirte, ARP Request Replay or WPS attack. This tool is in active development. SO, you can expect timely update with new features. Pro version of the tool is also available which offers much features. Download Fern Wi. Fi Wireless cracker http www. Co. WPAtty. Co. WPAtty is another nice wireless password cracking tool. It is an automated dictionary attack tool for WPA PSK to crack the passwords. It runs on Linux OS and offers a less interesting command line interface to work with. It runs on a word list containing thousands of password to use in the attack. If the password is in the passwords word list, this tool will surely crack the password. But this tool is slow and speed depends on the word list and passwords strength. Another reason for slow process is that the hash uses SHA1 with a seed of SSID. It means the same password will have a different SSIM. So, you cannot simply use the rainbow table against all access points. So, the tool uses the password dictionary and generates the hash for each word contained in the dictionary by using the SSID. This tool is simple to use with available commands. With the newer version of the tool Co. WPAtty tried to improve the speed by using a pre computed hash file to avoid the computation at the time of cracking. This pre computed file contains around 1. SSIDs. But for successful attack, your SSID must be in that list. If your SSID is not in those 1. Still, you can try this tool to see how it works. Download Co. WPAtty http sourceforge. Airjack. Airjack is a Wi Fi 8. It is used to perform DOS attack and MIM attack. This wireless cracking tool is very useful in injecting forged packets and making a network down by denial of service attack. This tool can also be used for a man in the middle attack in the network. This tool is popular and powerful both. Download Air. Jack http sourceforge. Wep. Attack. Wep. Attack is another working open source Linux tool for breaking 8. WEP keys. Like few other tools in the list, this tool also performs an active dictionary attack. It tests millions of words from its dictionary to find the working key for the network. Only a working WLAN card is required to work with Wep. Attack to perform the attack. Limited usability but works awesome on supported WLAN cards. Download Wep. Attack http wepattack. Net. Stumbler. Net. Stumbler is another wireless password cracking tool available only for Windows platform. It helps in finding open wireless access points. This tool is freely available. Basically Net. Stumbler is used for wardriving, verifying network configurations, finding locations with a poor network, detecting unauthorized access points, and more. This tool is not very effective now. Main reason is that last stable release of the tool was back in April 2. So, it does not work with 6. AircrackAireplay ng Under Packet Injection Monitor Mode in Windows. Update 6 2. 7 0. I just found out that the makers of aircrack ng just made this method easier. Two days after I wrote this article, they released a VMWare image of their entire suite of wireless penetration tools. So, instead of downloading and using the generic Back. Track ISO step 1 and 5 head over to Aircrack ng and obtain their version. Update II 6 2. 7 0. I guess packet injection under Windows is feasible after all The same time the VMWare aircrack ng image was released, they also revealed a new USB Wi. Fi adaptor that lets you inject and read packets natively in Windows without the virtualization layer. Whats more, you can use the Wireshark GUI instead of the aircrack ng command line. Personally, I would still go with the Alfa read more below since it has nantenna connector. But thats just me WEP enabled access point within a couple of minutes. That Digg article piqued our curiosity in high school. My friend and I read about how the FBI publicly demonstrated a successful wireless network crack in a minuscule amount of time. Inspired, we obtained a laptop and searched around our neighborhood for WEP encrypted wireless networks. Our plan was to show these local folks how easy it was to acquire their WEP key. Then, we would convince them that we were good, hirable technicians who could upgrade their Wi. Fi WEP encryption scheme to WPA. We spent literally three days practicing, trying to crack our own network with Windows tools. But in the end, our plan never materialized. Why We were too n. Linux. Crippled Windows Users. Ill say it once and Ill say it again, I hate being a Windows user. I hold great respect for computer hackers who are quick to grasp other operating systems, like Linux and OS X, without a problem. But I, having been weaned on Windows since the day I touched a computer, have a hard time operating those unfamiliar user interfaces or lack thereof. I mean, more than half of Linux is in the shell command line Aircrack ng Win. Binary Port. Many users like myself have a hard time integrating with the computer hacker world. Most programs are written for nix operating systems. Only when a kind, talented soul takes pity on us Windows amateurs and ports the code to Win. At the time, that Win. Even today, wireless network penetration software is still in the Linux stage. The main software suite, Aircrack ng, is just barely supported in Windows. When I tried the Windows port, it was slow, it did not accept my drivers, and it crashed numerous times. Basically, the Win. Virtualization Solution. Finally, I decided to just try aircrack ng in Linux. I bought some equipment and ran the Backtrack Live on CD Linux Distribution. After reading up on numerous Linux and aircrack ng documentation, I was finally able to crack my home network While I was writing about hacking the Windows Vista and t mobile free Wireless Internet authentication which is not no longer relevant with VMWare, I had an epiphany. The same technique I used with VMware could also be applied to aircrack ng I tried it out and after a lot of trial and error, I cracked my home network once again. This time it was in WindowsFrequently Asked Questions. So how did I do this Before you begin my tutorial, I suggest you read this FAQ for background information. Why aircrack ng Aircrack ng is the most popular wireless cracking suite. Because of that, it is the most compatible with different types of hardware, it offers more forum support, and it is on the cutting edge of the latest Wi. Fi hacking techniques. What are the main elements in cracking a wireless network Airodump ng Gather special faulty data necessary to crack a network. Aireplay ng Stimulate the base AP station to generate the special data for aireplay ng. Aircrack ng Take the data from airodump ng and, with statistical or brute force dictionary analysis, crack the keyPSK. Why is Windows inherently unable to crack wireless networks Special mostly unavailable patched drivers are required to use these programs. What about the Peek DriverFirst of all, the Peek Driver is special software written by the Wild. Pakets Airo. Peek, sort of a wireless network version of WiresharkEthereal. The bad thing about the Peek Driver is that it only allows you to read packets. Essentially, you can only use airodump ng and aircrack ng. Theoretically, you can crack a wireless network with only these two programs but it is very difficult, drawn out, and plain inefficient. Without the speeding aid of aireplay ng, cracking a wireless network may take days. Aireplay ng helps inject packets and manipulate the wireless network. Why does the Peek Driver not support aireplay ng This is because aireplay ng requires the network card to be in a special state called Monitor Mode. In normal operation, the network interface is in Managed Mode. The Windows NDIS API Network Driver Interface Specification does not support any extensions for wireless monitor mode. Therefore, the only drivers that allow Wi. Fi cards to be in monitor mode are in Linux. Ive heard of Windows tools that support packet injection. I have too. But I also heard that they cost upwards of 3. So then there still is a way to use aireplay ng in Windows with your hack Yes. Basically, you run Backtrack as a virtual machine in VMWare Player. Since VMWare supports passthrough USB, the Backtrack virtual machine can directly access a compatible USB wireless network adapter. Note that my method will only work with a USB adapter since the only passthrough that virtual machine programs support is with the USB interface, not PCI, mini. PCI, PCMCIA, PC Card, Express Card, etc. So, I wont need to know Linux commands and I will be presented with that familiar, friendly user interface that I am accustomed to in Windows Heavens no If you read the answer above, you know you will still be using Linux in Windows. This is just a convenience of not having to switch between reboots. You will still be unable to avoid the obscure Linux shell commands Hardware. Lets just cut to the chase. There is no reason to continue if you dont even own the correct hardware. Im sorry, but there is no workaround for this. Im a frugal person and I tried doing this the frugal way. It just doesnt work. If youre not willing to open your wallet, I would stop reading now. In my research and tests on compatible network adapters, there is only one with the least quirks and the least breakage for this operation. Get the Alfa USB AWUS0. S Network Adaptor with the threaded RP SMA antenna connector. USB Wi. Fi adapters with antenna connections are almost impossible to find. Usually you have to solder and mod the circuitry of another adapter to gain this functionality. Save yourself some trouble and just purchase this one. Now, if you could only find where to buy this elusive piece of equipment. I found mine at Data. Alliance, an onlinee. Bay store managed by a man name George Hardesty. If you know of any other worthy store, please comment at the end of this post. Hardesty supplies most of my wireless networking needs. His inventory is the most cutting edge and cheapest that I have come across. Take a look at his store. It includes one of the most comprehensive resources Ive read on wireless networking. Nevertheless, dont be tempted to purchase the high powered Alfa USB AWUS0. H WLAN Adapter. Ive used it twice It breaks easily and it is noisy.
2 Oracle WebLogic Server Issues. This chapter describes issues associated with Oracle WebLogic Server. It includes the following topics JDK 7 Certification. Cygwin Wikipedia. Cygwin SIG win2 is a Unix like environment and command line interface for Microsoft Windows. Cygwin provides native integration of Windows based applications, data, and other system resources with applications, software tools, and data of the Unix like environment. Thus it is possible to launch Windows applications from the Cygwin environment, as well as to use Cygwin tools and applications within the Windows operating context. Cygwin consists of two parts a dynamic link library DLL as an API compatibility layer in the form of a C standard library providing a substantial part of the POSIX API functionality, and an extensive collection of software tools and applications that provide a Unix like look and feel. Cygwin was originally developed by Cygnus Solutions, which was later acquired by Red Hat. It is free and open source software, released under the GNU Lesser General Public License version 3. 3 Today it is maintained by employees of Red Hat, Net. App and many other volunteers. DescriptioneditCygwin consists of a library that implements the POSIX system call API in terms of Win.  Penetration testing tools cheat sheet, a high level overview quick reference cheat sheet for penetration testing. Stack Overflow The Worlds Largest Online Community for Developers. GNU development toolchain including GCC and GDB to allow software development, and running of a large number of application programs equivalent to those on Unix systems. Programmers have ported many Unix, GNU, BSD and Linux programs and packages to Cygwin, including the X Window System, K Desktop Environment 3, GNOME,4Apache, and Te. X. Cygwin permits installing inetd, syslogd, sshd, Apache, and other daemons as standard Windows services, allowing Microsoft Windows systems to emulate Unix and Linux servers. Cygwin programs are installed by running Cygwins setup program, which downloads the necessary program and feature package files from repositories on the Internet. Setup can install, update, and remove programs and their source code packages. A complete installation will take in excess of 3. GB of hard disk space, but usable configurations may require as little as 1 or 2 GB. Efforts to reconcile concepts that differ between Unix and Windows systems include A Cygwin specific version of the Unix mount command allows mounting Windows paths as filesystems in the Unix file space. Initial mount points can be configured in etcfstab, which has a very similar format as on Unix systems, except that Windows paths appear in place of devices. Filesystems can be mounted in binary mode by default, or in text mode, which enables automatic conversion between LF and CRLF endings which only affects programs that open files without explicitly specifying text or binary mode. Cygwin 1. 7 introduced comprehensive support for POSIX locales and many character encodings, whereby the UTF 8. Unicode encoding became the default. Windows file names and other identifiers, which are encoded as UTF 1. ConnectorODBC is a standardized database driver for Windows, Linux, Mac OS X, and Unix platforms. Online Documentation MySQL ConnectorODBC Installation. Specs Pentium Dual 2. 2 64bit, 5 GB mem, Windows 7 64bit reqs Win7 x64, 1GB Memory, Administrator time Oracle Weblogic 5 min, Fusion Middleware 23 min setup, 16. Windows drive letters map to a special directory, so for example C appears as cygdrivec. The cygdrive prefix can be changed. Windows network paths of the form HOSTSHAREFILE are mapped to HOSTSHAREFILE. Windows paths can also be used directly from Cygwin programs, but many programs do not support them correctly, hence this is discouraged. Full featured dev and proc file systems are provided. Cygwin supports POSIX symbolic links, representing them as plain text files with the system attribute set. Cygwin 1. 5 represented them as Windows Explorershortcuts, but this has been changed for reasons of performance and POSIX correctness. Cygwin also recognises NTFS junction points and symbolic links and treats them as POSIX symbolic links, but it does not create them as their semantics are not fully POSIX compliant. The Solaris API for handling access control lists ACLs is supported and maps to the Windows NT ACL system. Special formats of etcpasswd and etcgroup are provided that include pointers to the Windows equivalent SIDs in the GECOS field, allowing for mapping between Unix and Windows users and groups. The fork system call for duplicating a process is fully implemented, but it does not map well to the Windows API. For example, the copy on write optimization strategy could not be used. 567 As a result, Cygwins fork is rather slow compared with Linux and others. That overhead can often be avoided by replacing uses of the forkexec technique with calls to the spawn functions declared in the Windows specific process. The Cygwin DLL contains a console driver that emulates a Unix style terminal within the Windows console. Cygwins default user interface is the bash shell running in the Cygwin console. The DLL also implements pseudo terminal pty devices. Cygwin ships with a number of terminal emulators that are based on them, including mintty, rxvt unicode, and xterm. These are more compliant with Unix terminal standards and user interface conventions than the Cygwin console, but are less suited for running Windows console programs. Various utilities are provided for converting between Windows and Unix paths and file formats, for handling line ending CRLFLF issues, for displaying the DLLs that an executable is linked with, etc. Apart from always being linked against the Cygwin DLL, Cygwin executables are normal Windows executables. This means that Cygwin programs have full access to the Windows API and other Windows libraries, which allows gradual porting of programs from one platform to the other. However, programmers need to be careful about mixing conflicting POSIX and Windows functions. The version of gcc that comes with Cygwin has various extensions for creating Windows DLLs, specifying whether a program is a windowing or console mode program, adding resources, etc. Support for compiling programs that do not require the POSIX compatibility layer provided by the Cygwin DLL used to be included in the default gcc, but as of 2. Min. GW w. 64 project. Cygwin is used heavily for porting many popular pieces of software to the Windows platform. It is used to compile Sun. Java, Open. Office. Libre. Office, and even web server software like Lighttpd and Hiawatha. 8Red Hat normally licenses the Cygwin library under the GNU Lesser General Public License version 3 with an exception to allow linking to any free and open source software whose license conforms to the Open Source Definition9 less strict than the Free Software Definition. Red Hat also sells commercial licenses to those who wish to redistribute programs that use the Cygwin library under proprietary terms. 91. HistoryeditCygwin began in 1. Steve Chamberlain, a Cygnus engineer who observed that Windows NT and 9. COFF as their object file format, and that GNU already included support for x. COFF, and the C library newlib. He thought it would be possible to retarget GCC and produce a cross compiler generating executables that could run on Windows. This proved practical and a prototype was quickly developed. The next step was to attempt to bootstrap the compiler on a Windows system, requiring sufficient emulation of Unix to let the GNU configureshell script run. A Bourne shell compatible command interpreter, such as bash, was needed and in turn a fork system call emulation and standard inputoutput. Windows includes similar functionality, so the Cygwin library just needed to provide a POSIX compatible application programming interface API and properly translate calls and manage private versions of data, such as file descriptors. Initially, Cygwin was called gnuwin. Gnu. Win. 32 project. The name was changed to Cygwin.
Penetration testing tools cheat sheet, a high level overview quick reference cheat sheet for penetration testing. Stack Overflow The Worlds Largest Online Community for Developers. GNU development toolchain including GCC and GDB to allow software development, and running of a large number of application programs equivalent to those on Unix systems. Programmers have ported many Unix, GNU, BSD and Linux programs and packages to Cygwin, including the X Window System, K Desktop Environment 3, GNOME,4Apache, and Te. X. Cygwin permits installing inetd, syslogd, sshd, Apache, and other daemons as standard Windows services, allowing Microsoft Windows systems to emulate Unix and Linux servers. Cygwin programs are installed by running Cygwins setup program, which downloads the necessary program and feature package files from repositories on the Internet. Setup can install, update, and remove programs and their source code packages. A complete installation will take in excess of 3. GB of hard disk space, but usable configurations may require as little as 1 or 2 GB. Efforts to reconcile concepts that differ between Unix and Windows systems include A Cygwin specific version of the Unix mount command allows mounting Windows paths as filesystems in the Unix file space. Initial mount points can be configured in etcfstab, which has a very similar format as on Unix systems, except that Windows paths appear in place of devices. Filesystems can be mounted in binary mode by default, or in text mode, which enables automatic conversion between LF and CRLF endings which only affects programs that open files without explicitly specifying text or binary mode. Cygwin 1. 7 introduced comprehensive support for POSIX locales and many character encodings, whereby the UTF 8. Unicode encoding became the default. Windows file names and other identifiers, which are encoded as UTF 1. ConnectorODBC is a standardized database driver for Windows, Linux, Mac OS X, and Unix platforms. Online Documentation MySQL ConnectorODBC Installation. Specs Pentium Dual 2. 2 64bit, 5 GB mem, Windows 7 64bit reqs Win7 x64, 1GB Memory, Administrator time Oracle Weblogic 5 min, Fusion Middleware 23 min setup, 16. Windows drive letters map to a special directory, so for example C appears as cygdrivec. The cygdrive prefix can be changed. Windows network paths of the form HOSTSHAREFILE are mapped to HOSTSHAREFILE. Windows paths can also be used directly from Cygwin programs, but many programs do not support them correctly, hence this is discouraged. Full featured dev and proc file systems are provided. Cygwin supports POSIX symbolic links, representing them as plain text files with the system attribute set. Cygwin 1. 5 represented them as Windows Explorershortcuts, but this has been changed for reasons of performance and POSIX correctness. Cygwin also recognises NTFS junction points and symbolic links and treats them as POSIX symbolic links, but it does not create them as their semantics are not fully POSIX compliant. The Solaris API for handling access control lists ACLs is supported and maps to the Windows NT ACL system. Special formats of etcpasswd and etcgroup are provided that include pointers to the Windows equivalent SIDs in the GECOS field, allowing for mapping between Unix and Windows users and groups. The fork system call for duplicating a process is fully implemented, but it does not map well to the Windows API. For example, the copy on write optimization strategy could not be used. 567 As a result, Cygwins fork is rather slow compared with Linux and others. That overhead can often be avoided by replacing uses of the forkexec technique with calls to the spawn functions declared in the Windows specific process. The Cygwin DLL contains a console driver that emulates a Unix style terminal within the Windows console. Cygwins default user interface is the bash shell running in the Cygwin console. The DLL also implements pseudo terminal pty devices. Cygwin ships with a number of terminal emulators that are based on them, including mintty, rxvt unicode, and xterm. These are more compliant with Unix terminal standards and user interface conventions than the Cygwin console, but are less suited for running Windows console programs. Various utilities are provided for converting between Windows and Unix paths and file formats, for handling line ending CRLFLF issues, for displaying the DLLs that an executable is linked with, etc. Apart from always being linked against the Cygwin DLL, Cygwin executables are normal Windows executables. This means that Cygwin programs have full access to the Windows API and other Windows libraries, which allows gradual porting of programs from one platform to the other. However, programmers need to be careful about mixing conflicting POSIX and Windows functions. The version of gcc that comes with Cygwin has various extensions for creating Windows DLLs, specifying whether a program is a windowing or console mode program, adding resources, etc. Support for compiling programs that do not require the POSIX compatibility layer provided by the Cygwin DLL used to be included in the default gcc, but as of 2. Min. GW w. 64 project. Cygwin is used heavily for porting many popular pieces of software to the Windows platform. It is used to compile Sun. Java, Open. Office. Libre. Office, and even web server software like Lighttpd and Hiawatha. 8Red Hat normally licenses the Cygwin library under the GNU Lesser General Public License version 3 with an exception to allow linking to any free and open source software whose license conforms to the Open Source Definition9 less strict than the Free Software Definition. Red Hat also sells commercial licenses to those who wish to redistribute programs that use the Cygwin library under proprietary terms. 91. HistoryeditCygwin began in 1. Steve Chamberlain, a Cygnus engineer who observed that Windows NT and 9. COFF as their object file format, and that GNU already included support for x. COFF, and the C library newlib. He thought it would be possible to retarget GCC and produce a cross compiler generating executables that could run on Windows. This proved practical and a prototype was quickly developed. The next step was to attempt to bootstrap the compiler on a Windows system, requiring sufficient emulation of Unix to let the GNU configureshell script run. A Bourne shell compatible command interpreter, such as bash, was needed and in turn a fork system call emulation and standard inputoutput. Windows includes similar functionality, so the Cygwin library just needed to provide a POSIX compatible application programming interface API and properly translate calls and manage private versions of data, such as file descriptors. Initially, Cygwin was called gnuwin. Gnu. Win. 32 project. The name was changed to Cygwin.
Downloads Citrix. Easily manage the Citrix portfolio of products from the cloud. Simplify control of your apps, desktops, content, devices and network. Explore Citrix Cloud services. These days I do not need a full FTP client as much as I used to several years ago. Part of this is just because we now tend to access everything over the Internet. Latest bug fixes for Microsoft Windows, including fixes for some possible DoS attacks.  Windows Windows Update is a wonderfully useful application that allows central management and automatic installation of updates for Windows Server 2003. There are. One of the most beneficial applications of using a computer is its remote desktop connection capabilities. A remote connection is when a computer user host computer. Wine is a free implementation of Windows on Unix. WineHQ is a collection of resources for Wine developers and users. I am running some small websites which are served by Apache Linux. Currently, I am trying to cut down the SSL configuration as far as possible to make it as secure.
Windows Windows Update is a wonderfully useful application that allows central management and automatic installation of updates for Windows Server 2003. There are. One of the most beneficial applications of using a computer is its remote desktop connection capabilities. A remote connection is when a computer user host computer. Wine is a free implementation of Windows on Unix. WineHQ is a collection of resources for Wine developers and users. I am running some small websites which are served by Apache Linux. Currently, I am trying to cut down the SSL configuration as far as possible to make it as secure. 
 I want to click a button on my access form that opens a folder in Windows Explorer. Is there any way to do this in VBA Back in September last year, I wrote this article about accessing FTP sites using Windows Vista. I then completely shifted to Windows 7 starting from M3 Build. Virtual Cloud Server Hosting VPS Great value combined with powerful features unlimited traffic. OS Linux MS Windows are available at cheap rates.
I want to click a button on my access form that opens a folder in Windows Explorer. Is there any way to do this in VBA Back in September last year, I wrote this article about accessing FTP sites using Windows Vista. I then completely shifted to Windows 7 starting from M3 Build. Virtual Cloud Server Hosting VPS Great value combined with powerful features unlimited traffic. OS Linux MS Windows are available at cheap rates.
SQL Server Express 2. Visual Studio 2. 01. March 1. 9, 2. 01. Madrigal. Database, Installation, MS SQL Server Express, Visual Studio 2. This tutorial will show you how to install MS SQL Express 2. RC and synch it up to Visual Studio 2. Before we start you will need the following. Visual Studio 2. 01. Must have SP1 installed prior to the MS SQL Server 2. Installation. MS SQL Express 2. Choose the version to download as Express and Tools. This will give you the the Database and MS SQL Server Management Studio Tools. Installation of MS SQL Express 2. Double click on the executable file that you downloaded. The program will start Extracting Files. You will get the following screen.  I selected New SQL Server NOTE If you have 2. SP2 of 2. 00. 8. Click Next on the following screen.
I selected New SQL Server NOTE If you have 2. SP2 of 2. 00. 8. Click Next on the following screen.  In the next screen accept the license agreement. In the Feature Selection I am keeping the defaults. Click Next. In the installation rules it will check to see if you have the latest Visual Studio 2. SP1. If you receive a Failed you will need to install the SP1 before you proceed. Click Next. After the installation Rules you will be presented with the following screen. I have selected to have the default instance. The default instance name comes up as MSSQLSERVER. Click Next. The next step analyzes your hard drive space. Click Next. The next screen shows the password for the accounts. This article explains how to easily install SQL Server 2012 in Windows 8. 1. I have left these blank. Since this is a local database that will not be used for production sites this is acceptable. Click Next. Now you are prompted to enter in a password. I have chosen Windows Authentication.
In the next screen accept the license agreement. In the Feature Selection I am keeping the defaults. Click Next. In the installation rules it will check to see if you have the latest Visual Studio 2. SP1. If you receive a Failed you will need to install the SP1 before you proceed. Click Next. After the installation Rules you will be presented with the following screen. I have selected to have the default instance. The default instance name comes up as MSSQLSERVER. Click Next. The next step analyzes your hard drive space. Click Next. The next screen shows the password for the accounts. This article explains how to easily install SQL Server 2012 in Windows 8. 1. I have left these blank. Since this is a local database that will not be used for production sites this is acceptable. Click Next. Now you are prompted to enter in a password. I have chosen Windows Authentication.  StepbyStep Build a FREE System Center 2012 Configuration Manager SP1 Lab in the Cloud. In this post, Ill guide you trough the process of installing Windows Server 2012 R2, SQL Server 2014 CTP1, and on top of that the brand new TFS 2013 that was. Comments Installing SharePoint 2013 on Windows Server 2012 and SQL Server 2012 Part 4 SQL Server Installation and Configuration Updated July 3, 2017. Ive purchased the SCCM installation guide, primarily complete a fresh installation of SCCM on Server 2012 R2 and SQL Server 2014 so we can migrate our current. I have also put my login as the SQL Server Administrator. Click Next. Click Next on the Error Reporting step. Then the installation rules will run. Hopefully no errors will show up. Click Next. Now the SQL Server is finally installing itself. This might take awhile, definitely enough time to grab a soda and a snack. After that you should see a bunch of items that were installed with the Success as the status. Click Close. You are now finished installed MS SQL Server 2. Express. SQL Server Management Studio Tools. When the MS SQL Server was installed it should have also installed the MS SQL Server Management Studio Tools. We will open that and add a new database. Open up the newly installed MS SQL Server Management Studio Express this should be in the Microsoft folder Microsoft SQL Server 2. Start Menu Programs. When it opens you are prompted to Connect to Server. The default should be, Windows Authentication. Click Connect. Here is what you should see. To add a database, right click on the Database Folder. You will see New Database Click on it. Insert the name for your new database. I will be naming mine Sample. DB for this particular tutorial. Click the Okay at the bottom of the page. Now you will see you new database in the menu. If you dont see it, right click on the Database folder and select Refresh. Right click on the Tables folder and select New Table. You will then be presented with a main section for creating a new table. I add one column called int. ID with a Datatype of INT for the puporse of this example. Click Save or ctrl S. You will then be prompted to name your table. I named mine Sample. Table. Expand your Table folder and you should now see you new table there. You have now set up a database and a table using the MS SQL Server Management Tools. Linking Visual Studio 2. Database. Open up your Visual Studio. On the menu at the top click the View option. Select the Server Explorer or use the short cut key ctrlW,L. This will open the following panel In the Server Explorer panel you will click on the small DB icon You will be prompted with the following screen. Select the Microsoft SQL Server option and click ContinueIn the following screen you will need to add the server and the database. We are keeping the Windows Authentication for the logon we set up the MS SQL Server with Windows Authentication. Click Okay. NOTE The server name is normally the name of your PC. Once you have clicked Okay you should see this in your Visual Studio 2. Server Explorer. Congratulations you have linked up your Visual Studio 2. MS SQL Server 2. 01. Database, MS SQL Express 2. SQL, SQL Server Management Tools, Visual Studio 2.
StepbyStep Build a FREE System Center 2012 Configuration Manager SP1 Lab in the Cloud. In this post, Ill guide you trough the process of installing Windows Server 2012 R2, SQL Server 2014 CTP1, and on top of that the brand new TFS 2013 that was. Comments Installing SharePoint 2013 on Windows Server 2012 and SQL Server 2012 Part 4 SQL Server Installation and Configuration Updated July 3, 2017. Ive purchased the SCCM installation guide, primarily complete a fresh installation of SCCM on Server 2012 R2 and SQL Server 2014 so we can migrate our current. I have also put my login as the SQL Server Administrator. Click Next. Click Next on the Error Reporting step. Then the installation rules will run. Hopefully no errors will show up. Click Next. Now the SQL Server is finally installing itself. This might take awhile, definitely enough time to grab a soda and a snack. After that you should see a bunch of items that were installed with the Success as the status. Click Close. You are now finished installed MS SQL Server 2. Express. SQL Server Management Studio Tools. When the MS SQL Server was installed it should have also installed the MS SQL Server Management Studio Tools. We will open that and add a new database. Open up the newly installed MS SQL Server Management Studio Express this should be in the Microsoft folder Microsoft SQL Server 2. Start Menu Programs. When it opens you are prompted to Connect to Server. The default should be, Windows Authentication. Click Connect. Here is what you should see. To add a database, right click on the Database Folder. You will see New Database Click on it. Insert the name for your new database. I will be naming mine Sample. DB for this particular tutorial. Click the Okay at the bottom of the page. Now you will see you new database in the menu. If you dont see it, right click on the Database folder and select Refresh. Right click on the Tables folder and select New Table. You will then be presented with a main section for creating a new table. I add one column called int. ID with a Datatype of INT for the puporse of this example. Click Save or ctrl S. You will then be prompted to name your table. I named mine Sample. Table. Expand your Table folder and you should now see you new table there. You have now set up a database and a table using the MS SQL Server Management Tools. Linking Visual Studio 2. Database. Open up your Visual Studio. On the menu at the top click the View option. Select the Server Explorer or use the short cut key ctrlW,L. This will open the following panel In the Server Explorer panel you will click on the small DB icon You will be prompted with the following screen. Select the Microsoft SQL Server option and click ContinueIn the following screen you will need to add the server and the database. We are keeping the Windows Authentication for the logon we set up the MS SQL Server with Windows Authentication. Click Okay. NOTE The server name is normally the name of your PC. Once you have clicked Okay you should see this in your Visual Studio 2. Server Explorer. Congratulations you have linked up your Visual Studio 2. MS SQL Server 2. 01. Database, MS SQL Express 2. SQL, SQL Server Management Tools, Visual Studio 2.
The stand is a full 8 ft. long, in order to provide generous support tables on either side of the saw. They'll help you cut down long stock with ease. Resources for Colorado based woodworkers, woodworking businesses, suppliers or other resources for woodworking in the state of Colorado.